Onion Router or Tor is a network that allows a user to remain anonymous on the internet and get rid of any possible surveillance, location monitoring, etc. while using the internet, we can access the Tor network with the help of a modified ESR Mozilla Firefox web browser.
Tor browser allows a person to browse the web anonymously by veiling the actual identity of the user. It protects the user from any traffic analysis and network spying. Tor is perhaps the most popular and secure option available to connect anonymously to the Internet. To reduce the confusion, let’s start by explaining what the Tor network is.
History of Tor
Tor uses the principle of “onion routing“, developed by Paul Syverson, Michael G. Reed and David Goldschlag at the US Naval Research Laboratory in the 1990s. The alpha version of Tor, called “ The Onion Routing Project ” or simply TOR Project, was developed by Roger Dingledine and Nick Mathewson; it was launched on September 20, 2002. Further developments were carried out under the financial roof of the Electronic Frontier Foundation (EFF).
The Tor Project Inc. is a non-profit organization that currently maintains the browser and is responsible for its development. It has received funding mainly from the US government and additional aid from the Swedish government and various NGOs and individual sponsors.
How does Tor work?
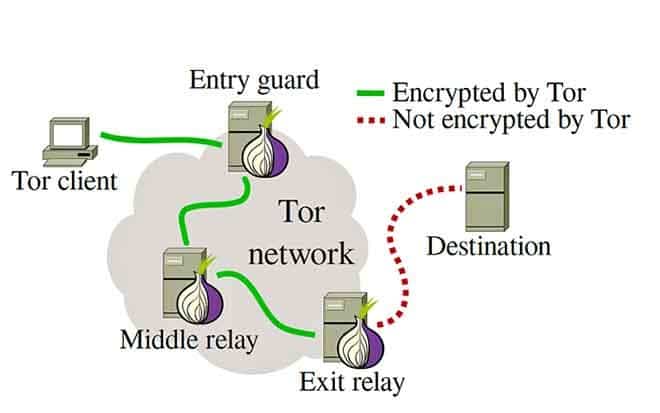
How to use Tor? The answer to how it works or how to use it is quite simple. The browser uses the concept of the “onion routing” method in which user data is first encrypted and then transferred through different nodes in the Tor network. Therefore, it creates multi-layered encryption (layers like an onion) and keeps the user’s identity safe.
Tor is a network that implements a technique called Onion Routing, designed with the goal of securing communications in the United States Navy. The idea is to change the traditional Internet routing mode to ensure anonymity and confidentiality of data.
The traditional routing we use to connect to servers on the internet is simple. For example, if you want to read a website, your computer connects directly to its servers. The path is relatively simple- from your computer to your router, from there to the routers of your ISP (Internet provider), and then directly to the servers of the web, you are visiting.
The downside is that if someone intercepts the data packets somewhere in between, they will know exactly where they are coming from and where they are going. Even though the data for each packet is encrypted on HTTPS pages, the packet headers are not encrypted and the sender and recipient fields (among others) are still visible.
One encryption layer is decrypted at each subsequent Tor node and the remaining data is forwarded to any random node until it reaches the destination server. For the target server, the last Tor node/exit relay appears as the source of the data. It is therefore difficult to trace the identity of the user or server by any surveillance system acting as an intermediary.
In addition to providing anonymity for autonomous users, Tor can also provide anonymity to websites and servers in the form of Tor Hidden Services. Additionally, P2P applications such as BitTorrent can be configured to use the Tor network and download torrent files.
How does Tor browser work?
Tor Project Inc. has released the Browser, which is a modification of an Extended Support Release (ESR) version of the Mozilla Firefox browser. The browser is portable so that it can be used by external media and it also reduces the kernel of the installation.
Tor removes your browsing history and cookies after each use, thus reducing the risk of any tracking by cookies. We can set up SOCKS (Socket Secure) based applications to use the Tor network by configuring them with a loop-back address.
It is also known as the dark web browser as it allows users to browse so-called dark websites that are not accessible on the normal web. The Tor browser is available for various desktop operating systems, including Windows, Linux, and macOS. You can visit this link to download the latest version of Tor Browser Italiano for Windows, Linux, and macOS.
How to download the Tor browser?
How to install Tor on Windows 10/7/8?
- Run the Tor browser setup.
- Choose your desired language.
- In the next window, choose the destination folder. Using Tor would be easy if you choose the desktop as the destination.
- Click Install.
The Tor configuration will create a folder named Tor Browser on the desktop. Open the folder and run the shortcut file. For Linux, you will need to extract the downloaded file, using the command line or a file extraction application.
Download Tor browser English
Tor Browser Android
- Tor Browser Download – official Tor app for Android
- Orbot – a free proxy app with Tor for Android devices.
- Orfox – a mobile version of Tor Browser for Android devices. (Out of production)
- The Guardian Project, a global developer community founded by Nathan Freitas, must be credited for the development of Orfox.
Tor Browser iOS
- Tor Browser iOS created by Tor Project core collaborator Mike Tigas.
Tor browser Windows PC
It is normal that browsing with Tor is extremely slow, which is due to the anonymization encryption of the network itself. This is why you will also notice that most of them seem to have been created two decades ago since they are usually created in plain HTML and without too many frills.