Security flaws and loopholes are to be found almost on a daily basis. These are most common in software. When it comes to Linux kernel, it’s rare that security flaws happen. But now millions of Linux OS running systems have been affected by a vulnerability.
According to a report, machines running on Linux kernel versions prior to 5.0.8 have been affected by a race condition vulnerability which is leading to remote attacks. If we talk about race condition in simple words then race condition occurs when a system is made to perform a task in a particular sequence is forced to perform two or more tasks simultaneously.
The attackers can exploit the vulnerability found in the Linux kernel’s rds_tcp_kill_sock TCP/IP implementation in net/rds/tcp.c. This security flaw can be used to launch DoS states and to run code remotely on Linux machines which have been found to be vulnerable.
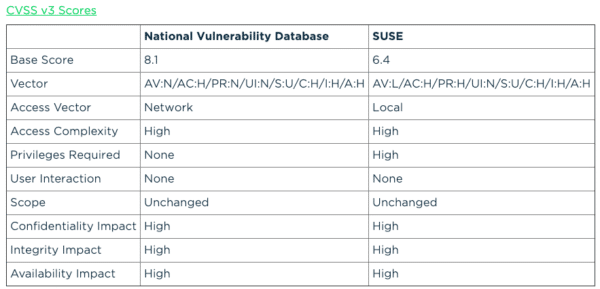
This vulnerability has been assigned with a high severity base score of 8.1 by NIST’s NVD. This vulnerability is being called as CVE-2019-11815 with a high impact score of 5.9. More information regarding this flaw can be found from the official sites of different Linux distributions such as Red Hat, Ubuntu, SUSE, and Debian.
According to Bleeping Computer, the attackers can implement the attack with the help of specially crafted TCP packets sent to vulnerable Linux boxes to execute arbitrary codes on the targeted Linux system.
According to CVSS 3.0, the attackers can take advantage of this vulnerability and can get access to all resources, edit all the files and can stop accessing the resources after successfully exploiting the system.
The good news is that this issue has been already fixed the end of the March month with the release of Linux kernel 5.0.8. If you don’t want your Linux system to get exploited then it is highly advised to update your kernel as fast as possible and also install the recommended patches.