A new family of Android ransomware has emerged, which spreads by SMS. This is happening after two years of decline in Android ransomware. The new Android ransomware named Android/Filecoder.C has been detected by ESET Mobile security researchers.
How did this Ransomware spread?
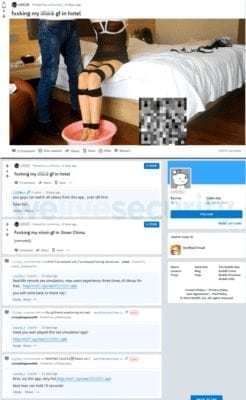
Initially, the new ransomware Android/FileCoder.C got distributed via various online forums like Reddit, XDA Developers etc. This malware has been active since at least July 12th, 2019.
Bad content links and QR codes are being provided on these forums to entice the users to click on it and activate the malware. The attackers are using Bitly to shorten the malicious links so that they look authentic and receive more clicks.
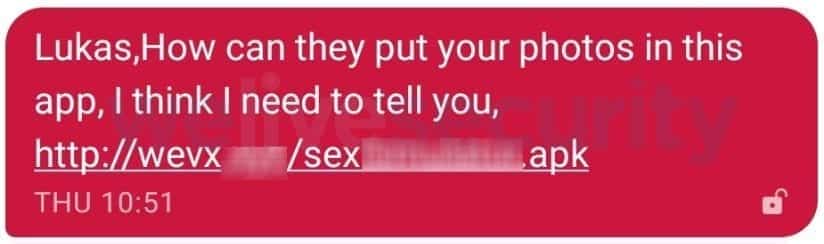
Android/FileCoder.C tries to gain access to the phone’s contacts and spreads further via SMS with malicious links. These links redirect users to download and install a ransomware-infected app. These are mostly s3x simulator apps. You will also find that the message has some texts related to your photos which force you to click on that link.
You will find this malware in 42 different languages which spreads according to the infected device default language. In order to reach and attract more people. this malware uses the user’s contact names as a prefix.
How does Android/FileCode.C Ransomware work?
The process starts when a user receives a malicious SMS message and he or she clicks on the link provided in that message. The link redirects the user to download the app and install it on the phone. And when the app is launched, it displays a s3x simulator online game. However, Its main purpose is not to show anything but to start C&C communication, spread the malicious message to more people and carry out the encryption/decryption mechanism.
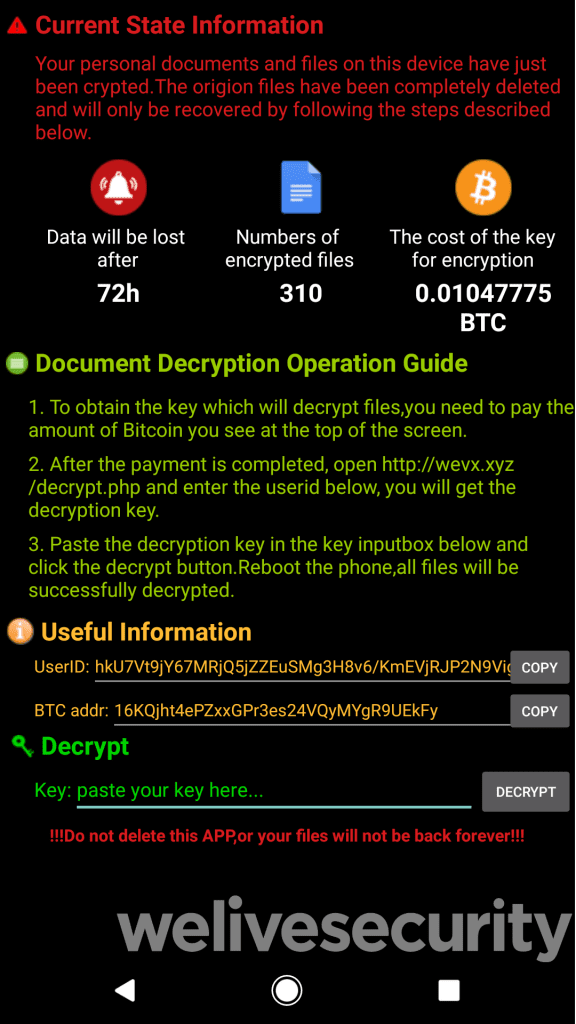
The C&C (commands and control) server is used by the attackers to get access to the hardcoded C&C and Bitcoin addresses. Once, it is done, the files are then encrypted. After the encryption, the user is asked to complete the payment to decrypt the files. And the user is also warned that if the app is uninstalled than all the encrypted files will be deleted forever. It is to be noted that .zip and .zar files are not affected by this malware.
According to the researchers, the impact of the Android/FileCoder.C ransomware is limited due to narrow targeting and poor the execution of the campaign. But if this ransomware had reached to many users, it would have become a serious threat.